Which of the Following Are Parts of the Opsec Process
Identify your sensitive data including your product research intellectual property financial statements customer information and employee information. Step 1 Identify Critical Information.
What Is Opsec Operations Security
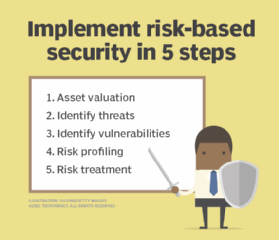
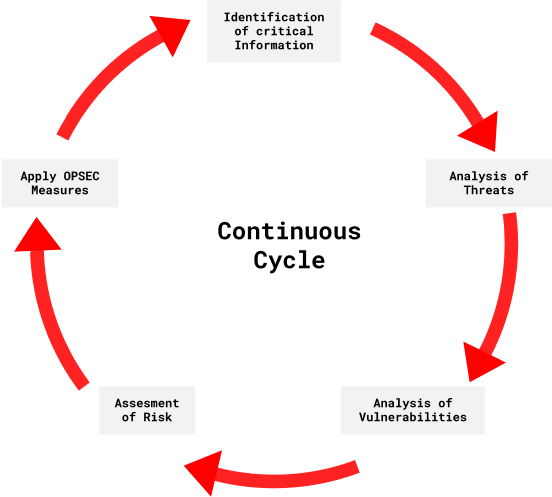
1 identification of critical information 2 analysis of threats 3 analysis of vulnerabilities 4 assessment of risk and 5 application of appropriate countermeasures.

. The information that youre looking here should be critical to your surroundings and whats going on as well as your intentions abilities activities etc. - Analysis of threats. 1 identification of critical information 2 analysis of threats 3 analysis of vulnerabilities 4 assessment of risk and 5 application of appropriate countermeasures.
Which of the following are parts of the OPSEC process. OPSEC is an analytical process used to deny an adversary information generally unclassified concerning our intentions and capabilities by identifying controlling and protecting indicators associated with our planning processes or operations. Advertisement Advertisement New questions in Computers and Technology.
Analysis of threats application of appropriate countermeasures conduct vulnerability assessments Most relevant text from all around the web. The OPSEC process involves five steps. - Application of appropriate countermeasures.
Analysis of threats application of appropriate countermeasures conduct vulnerability assessments. - Analysis of vulnerabilities. OPSEC Process Five Steps - Identification.
Select all that apply. OPSEC Process. The OPSEC process is most effective when its fully integrated into all planning and operational processes.
It involves five steps. NSDD 298 required all executive departments and agencies with national security operations and the contractors that support them to establish OPSEC programs. Add your answer and earn points.
Which of the following are parts of the OPSEC process. See answer 1 Best Answer. Which of the following must be reported.
Which of the following materials are subject to pre-publication review. The very first step of the OPSEC process is to identify any information that pertains to the situation youve found yourself in. Interagency OPSEC Support Staff IOSS was.
This will be the data you will need to focus your resources on protecting. The OPSEC process involves five steps. Which of the following are parts of the opsec process 1 See answer Advertisement Advertisement CrazyKitty7450 is waiting for your help.
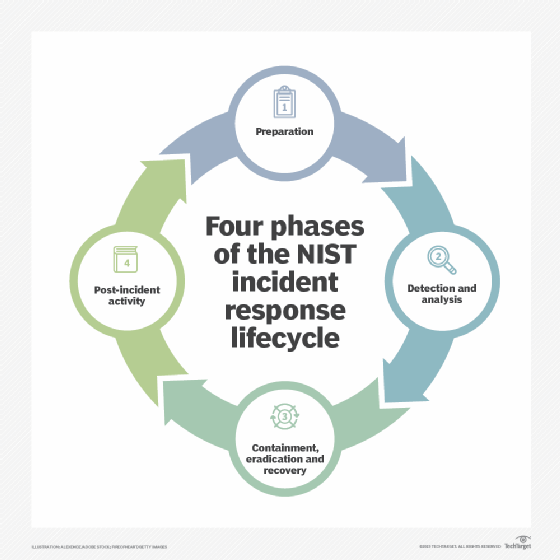
The processes involved in operational security can be neatly categorized into five steps. Identifying critical information Analyzing threats to that information Examining vulnerabilities to those threats. OPSEC Background National Security Decision Directive NSDD 298 identified and formalized the five-step OPSEC process.
I dont know the parts of the opsec process. Answer Which of the following are parts of the OPSEC process. The OPSEC process is most effective when fully integrated into all planning and operational processes.
Tryhackme Red Team Opsec Write Up Summary Infosec Cafe

Geothermal Greenhouse Update Dec 9 2015 Aquaponics Aquaponics System Aquaponics Diy

Hidden Bookshelf Door Complete Tutorial Gary Katz Online Hidden Door Bookcase Bookshelf Door Hidden Door
Operations Security Opsec Nttp 3 13 3m Mctp 3 32b By Department Of The Navy Paperback Barnes Noble

Amazon Com Operations Security Opsec Ebook Us Army Www Survivalebooks Com Kindle Store

What Is Operational Security The Five Step Opsec Process Securitystudio

Make Internet Safer With Dns Firewall Implementation Case Study At

Pin By Mery D Amico On Wood Shop Items To Do Maybe Try Hidden Door Bookcase Door Secret Rooms
Tryhackme Red Team Opsec Write Up Summary Infosec Cafe

Operations Security Opsec A Critical Tool For Enterprise And Personal Security Tactiks Rapid Reference Tools Reiken Stuart 9798682617678 Amazon Com Books

Opsec For Android Apk Download

Cyber Security How To Avoid Opsec Violations Mountain Home Air Force Base News
What Is Opsec Operations Security
Online Privacy Through Opsec And Compartmentalization Part 3

What Is Operations Security Opsec Upguard

The Glory Days Of Groundnut Peanut Pyramids In Nigeria Healthy Benefits Ingredients Recipes Honey Roasted

What Is Opsec Operations Security

Comments
Post a Comment